Trend Micro AWS Built-In module
This document walks you through the process of deploying the Trend Micro AWS Built-In (ABI) module to the AWS Cloud. It’s intended for customers who are using the cfn-abi-trend-cloudone ABI and building an ABI project.
The AWS Built-In program validates solutions that are integrated with relevant AWS foundational services such as identity, management, security, and operations. This program helps customers find and deploy a validated solution that addresses specific customer use cases while providing visibility and control of AWS native service integrations.
Next: Overview
Subsections of Trend Micro AWS Built-In module
Overview
This ABI deploys Trend Micro integrations for AWS Organizations to the AWS Cloud. It’s for cloud operations, SecOps, cloud builders, and others who want to implement security across multiple AWS accounts. If you are unfamiliar with AWS Built-In, refer to AWS Built-In.
Deploying this ABI package does not guarantee an organization’s compliance with any laws, certifications, policies, or other regulations.
Security outcomes
The Trend Micro AWS Built-In module can be used to help you set up two different security outcomes across your organization.
AWS CloudTrail analysis
The XDR capability of Trend Micro Vision One applies effective expert analytics and global threat intelligence using data collected across multiple vectors, such as emails, endpoints, servers, cloud workloads, and networks. It can also analyze the AWS CloudTrail logs from your AWS accounts, identify threats and attacks, alert you to problems, and create a visualization of the log.
This ABI module integrates your organizational trail with Trend Vision One, which helps ensure that all CloudTrail events across all accounts in your organization are analyzed by Vision One.
EC2 instance security agent deployment via SSM
Distributor is an integrated feature of AWS Systems Manager that you can use to store and distribute software packages in your accounts. By integrating Workload Security with AWS Systems Manager Distributor, you can distribute Cloud One Workload Security agents across multiple platforms, control access to managed instances, and automate your deployments.
This ABI module is deployed across either selected or all accounts and Regions. It helps ensure that the Trend Cloud One Workload Security agent deploys to your targeted EC2 instances.
AWS Marketplace listings
Next: Terminology
Terminology
- ABI : AWS Built-In (ABI).
- ABI modules: GitHub repositories based on AWS SRA, which provide templates for enabling AWS foundational services such as AWS CloudTrail, Amazon GuardDuty, AWS Security Hub, and other security services.
- ABI projects: The GitHub repositories built by partners in collaboration with AWS. While building these projects, partners use ABI modules to enable AWS services as needed before creating partner-specific assets. A project contains the following:
- IaC templates to automate enablement of both AWS and partner services
- Wrappers for common formats like CfCT manifest, SC baselines, and others to allow customers to pick and choose available services. For this package, we focus on including only the CfCT manifest file.
- Trend Cloud One: A platform built for cloud builders, where you can secure your cloud infrastructure.
- Trend Vision One: A platform that enhances and consolidates detection, investigation, and response capabilities across emails, endpoints, servers, cloud workloads, and networks.
Next: Cost and licenses
Costs and licenses
Trend Micro licensing costs
For current pricing, refer to Trend Cloud One and Trend Enterprise Security Solutions on AWS Marketplace.
AWS service costs
Next: Architecture
Architecture
Deploying this ABI package with default parameters builds the following architectures.
AWS CloudTrail integration architecture diagram
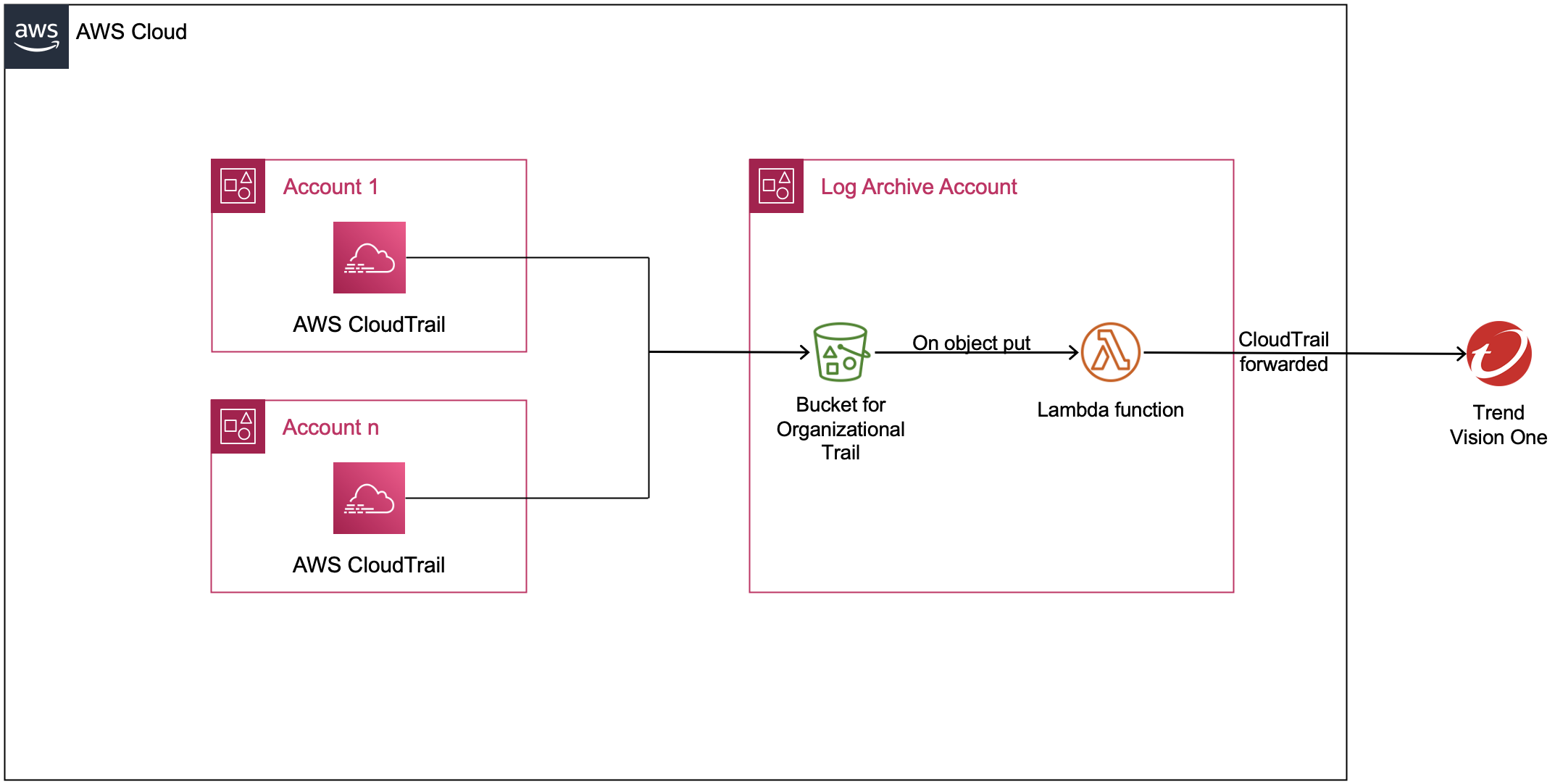

As shown in the diagram, this integration sets up the following:
- In the log archive account:
- Amazon CloudWatch events rules to detect new PUTs in the organizational CloudTrail S3 bucket and trigger an AWS Lambda function.
- The Lambda function forwards the new CloudTrail events to Trend Vision One.
SSM integration architecture diagram
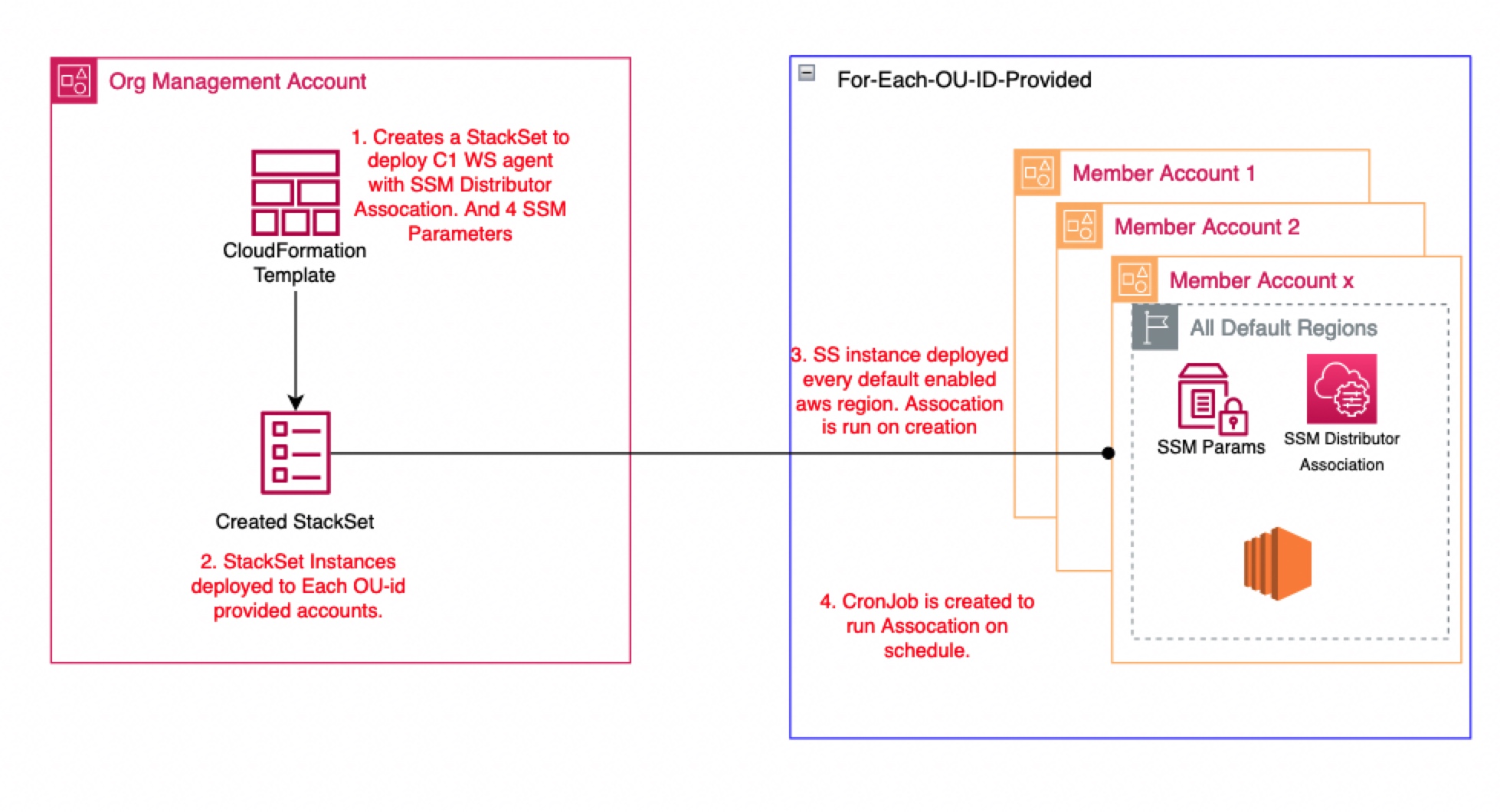

- In each AWS Organizations account:
- Four system-manager parameters are created in each AWS Region.
- For a defined CRON job, the AWS Systems Manager workload security agent association package triggers for ‘*’ instances managed by SSM.
- The SSM association package deploys workload security agent for unmanaged instances.
Next: Deployment Options
Deployment options
Deployment options supported by this ABI package
The ABI package supports the following options:
Next: Predeployment steps
Predeployment options
Before deploying this ABI package, complete the following steps:
Next: Deployment Steps
Deployment steps
Launch the CloudFormation template in the AWS Organizations management account
-
Download the CloudFormation template to your local machine.
-
Launch the CloudFormation template in your AWS Control Tower home Region.
- Stack name:
template-trend-micro-enable-integrations
- List parameters with [call out default values and update below example as needed]
- Mandatory parameters
- Parameters for the ABI module:
- DeployCloudTrailIntegration:
true
- DeploySSMIntegration:
true
- DeploySecurityHubIntegration:
true
- Parameters related to the CloudTrail integration:
- Parameters related to the SSM integration:
- CronJob:
cron(15 10 * * ? *)
- AccountAdminStatus:
SELF
- Parameters related to the Security Hub integration:
- EnableSecurityHub: Set to
false unless you don’t have Security Hub enabled. Set to true to enable Security Hub in the audit account.
-
Choose both the Capabilities and then Submit to launch the stack.
[] I acknowledge that AWS CloudFormation might create IAM resources with custom names.
[] I acknowledge that AWS CloudFormation might require the following capability: CAPABILITY_AUTO_EXPAND
Wait for the CloudFormation status to change to CREATE_COMPLETE.
Launch using Customizations for Control Tower
CfCT combines AWS Control Tower and other highly available, trusted AWS services to help customers more quickly set up a secure, multiaccount AWS environment according to AWS best practices. You can add customizations to your AWS Control Tower landing zone using an AWS CloudFormation template and service control policies (SCPs). You can deploy the custom template and policies to individual accounts and organizational units within your organization.
CfCT also integrates with AWS Control Tower lifecycle events to help ensure that resource deployments stay in sync with your landing zone. For example, when a new account is created using the AWS Control Tower account factory, CfCt helps to ensure that all resources attached to the account’s organizational unit are automatically deployed.
The templates provided as part of the ABI packages are deployable using CfCT. For more information, refer to Prerequisites.
Prerequisites
- For CfCT to launch resources from the management account, you must create a role with necessary permissions in that account.
How it works
To deploy this integration page using CfCT, add the following blurb to the manifest.yaml file, and update the accounts and organizational units as needed.
resources:
- name: sra-enable-partner1-solution
resource_file: https://aws-abi.s3.us-east-1.amazonaws.com/cfn-abi-trend-cloudone/templates/main.template.yaml
deploy_method: stack_set
parameters:
- parameter_key: pProductArn
parameter_value: arn:aws:securityhub:us-east-1::product/cloud-custodian/cloud-custodian
- parameter_key: pSRASourceS3BucketName
parameter_value: aws-abi
- parameter_key: pSRAStagingS3KeyPrefix
parameter_value: cfn-abi-aws-reference-guide
- parameter_key: CloudOneApiKey
parameter_value: Your Cloud One API key. For more information, refer to [Manage API keys](https://cloudone.trendmicro.com/docs/identity-and-account-management/c1-api-key/).
- parameter_key: OrganizationId
parameter_value: Your AWS Organization ID. For more information, refer to [Viewing details about your organization](https://docs.aws.amazon.com/organizations/latest/userguide/orgs_manage_org_details.html).
- parameter_key: DeployCloudTrailIntegration
parameter_value: true
- parameter_key: DeploySSMIntegration
parameter_value: true
- parameter_key: DeploySecurityHubIntegration
parameter_value: true
- parameter_key: VisionOneAuthenticationToken
parameter_value: Vision One authentication token. For more information, refer to [Obtaining API Keys for Third-Party Apps](https://docs.trendmicro.com/en-us/enterprise/trend-vision-one-olh/administrative-setti/user-accounts/obtaining-api-keys-f_001.aspx).
- parameter_key: VisionOneRegion
parameter_value: Vision One Region. For more information, refer to [Regional Domains](https://automation.trendmicro.com/xdr/Guides/Regional-Domains).
- parameter_key: ExistingOrganizationalCloudtrailBucketName
parameter_value: Bucket name of an existing Organizational CloudTrail. For more information, refer to [Creating a trail for an organization](https://docs.aws.amazon.com/awscloudtrail/latest/userguide/creating-trail-organization.html).
- parameter_key: CronJob
parameter_value: cron(15 10 * * ? *)
- parameter_key: AccountAdminStatus
parameter_value: SELF
- parameter_key: EnableSecurityHub
parameter_value: false
deployment_targets:
accounts:
- [[MANAGEMENT-AWS-ACCOUNT-ID]]
Next: Postdeployment options
Postdeployment options
Verifying the solution functionality
Verifying the solution functionality depends on what modules and integrations you deployed in the previous step.
Verifying CloudTrail analysis
- Log in to your Trend Cloud One account.
- Choose Integrations at the bottom of the page and then Trend Vision One from the left-hand side of the page.
- Verify that the status of AWS CloudTrail is Connected.
- Log in to your Vision One account.
- In the Trend Vision One console, navigate to XDR Threat Investigation > Search.
- Change the search method to Cloud Activity Data.
- Locate your CloudTrail data. For example, use the following search string:
*
- The presence of data means that the CloudTrail analysis deployed successfully.
Verifying EC2 instance security agent deployment via SSM
- Log in to your Trend Cloud One account.
- Choose Endpoint & Workload Security, and then choose the Computers tab.
- Verify that the Agent Status Light Column has a green indicator.
- A green indicator means the agent deployed successfully.
Next: Test the deployment
Test the deployment
Follow the steps provided in Postdeployment options.
Next: Additional resources
Additional resources
Partner documentation
AWS services
FAQs
Info
The FAQ is empty right now but will be updated as questions from customers come in after release.
Refer to the FAQs page.
Other documentation
Next: Troubleshooting
Troubleshooting
Common ABI issues
For troubleshooting common ABI issues, refer to the AWS Built-In General Information Guide and Troubleshooting CloudFormation.
SSM integration
No green indicator
- Log in to your AWS account.
- Navigate to Systems Manager > Parameter Store, and confirm that the four created parameters exist.
- Navigate to Systems Manager > State Manager.
- For agent association details, choose Association ID > Execution History > Failed execution.
Next: Feedback
Feedback
To submit feature ideas, report bugs, or submit feedback, use the Issues section of the GitHub repository for this ABI module. To submit code, refer to the AWS Built-in Reference Guide. To submit documentation feedback, use the following GitHub links:
To submit documentation feedback, use the following GitHub links:
Next: Notices
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible assessing the information in this document and any use of AWS products or services, each of which is provided “as is” without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the “License”). You may not use this file except in compliance with the License. A copy of the License is located at http://aws.amazon.com/apache2.0/ or in the accompanying “license” file. This code is distributed on an “as is” basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.
Cleanup instructions
Cleanup instructions
Delete the parent CloudFormation stack. No other actions are necessary.
FAQs
How do I contribute to this repository?
This solution is covered under Apache License version 2.0 (the “License”). For problems, submit a GitHub Issue. If you want to contribute a fix or enhancement, submit a GitHub pull request with your changes. All pull requests are reviewed before being merged.

